If there were a power cut right now, the whirring of your computer would stop. You would wait frustrated for systems to get back online, whilst hoping the document you were working on had AutoSaved shortly before the power switched off.
Now let’s upscale that scenario. In place of the power cut, let’s envisage a cyber-attack. Instead of your system being down for minutes, we’re now looking at hours. This time it’s not just you, not just your office but your entire business, both its internal and external facing operations. Not only is it a matter of restoring the power and carrying on, there remains uncertainty as to whether the system works, is it secure and can it be trusted? Has any data been corrupted in the meantime?
Cyber-attacks are becoming more prevalent. Government research has shown that 46 per cent of all UK businesses suffered a cyber security breach in 2016, a figure rising to 68 per cent in large firms. Furthermore, as businesses become increasingly dependent on technology, the impact of attacks is becoming more damaging.
The significance of cyber-attacks on UK businesses is clearly evident when looking at the growing use of online facilities utilised by the majority of businesses operating out of the UK.
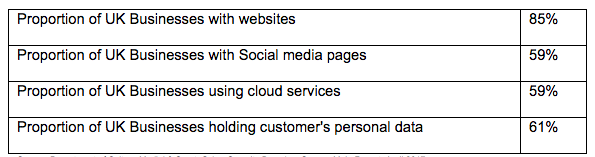
Source: Department of Culture Medial & Sport, Cyber Security Breaches Survey, Main Report, April 2017
Now imagine that you lost access to, and potentially control of, all of the above. For many businesses technology is the key link to market and, in many circumstances, it is the principal reflection of their brand and values. A victim of a cyber-attack may be unable to communicate with partners, suppliers or customers, with ramifications in both the short and long term.
Of the 781 businesses that reported a breach in the last 12 months, the impact on businesses was generally comprised of one, or more, of eight scenarios:
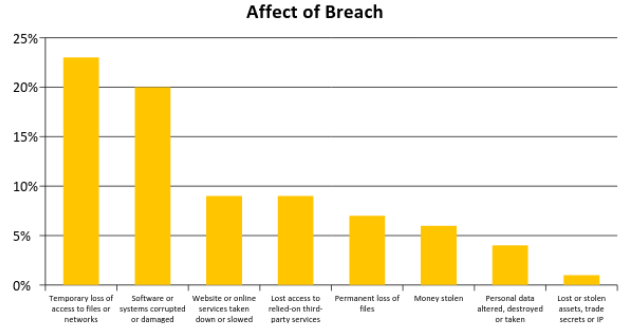
Source: Department of Culture Medial & Sport, Cyber Security Breaches Survey, Main Report, April 2017
The impact of the breach is similarly varied, of the same 781 incidents the impact was reported as follows:
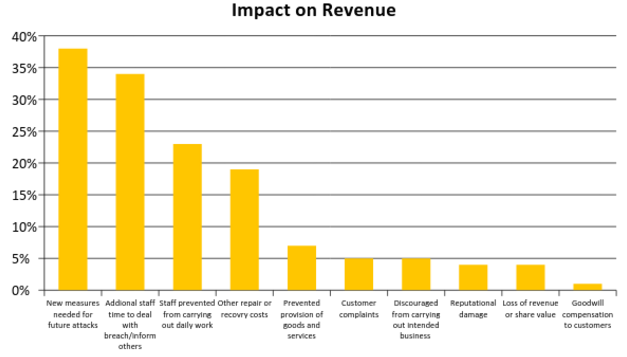
Source: Department of Culture Medial & Sport, Cyber Security Breaches Survey, Main Report, April 2017
The recent problems faced by British Airways, whilst not being caused by a cyber-attack, highlight the disruption to business that can be caused by a mass IT failure and the loss of revenue that can be suffered.
Hypothetically, a consumer may be looking to purchase an item or service from a business with an online sales facility. Unfortunately, as a result of a cyber-attack the website is offline. The customer elects to purchase the item online elsewhere, also picking up a few items that were not on their original shopping list. At the checkout screen they tick the box to receive additional emails about future promotions. In the coming months they continue to receive notifications of offers, resulting in numerous repeat purchases. Add to that the risk of adverse publicity through word of mouth, or more pertinently social media, and the impact of the single cyber-attack may have ramifications with a ‘long tail’ which may lose a business a significant amount of money in the months or years ahead.
Historically businesses have been able to insure against business interruption when this has resulted from physical damage to their buildings and/or systems, however, in such circumstances it is far easier to identify what goods and services have been impacted and/or damaged. However, when dealing with the impact of a cyber-attack businesses may find it far harder to calculate their losses, particularly with regards to their customer facing operations.
In order to assess a business’s losses many cyber breach insurance policies address business interruption by considering the turnover of the affected business over a period of 6 months, following the breach, against the business’s past results, taking into account market fluctuations and thereafter calculate the likely loss in turnover. However, as technology and automation becomes a more significant factor in every facet of business, the potential losses stemming from business interruption are likely to grow.
This is why care should be taken to record every aspect of a cyber-attack. Organisations quickly focus on solving the problem and restoring systems. In the rush, they sometimes forget to record the harmful events as they happen. A common mistake when re-starting systems is to overwrite the audit trail of what has happened. This ‘rush to fix’ can make quantification of losses difficult if not impossible, and is often caused by not having a properly resourced and experienced incident response team.
Without this information, full claims to recover losses cannot be made against the perpetrators, insurers or outsourced service providers whose security measures may have failed. Moreover, unless one knows the harm suffered, it is difficult to design a proportionate response which is increasingly a requirement of regulators. Finally, realising what has been lost makes it easier to justify expenditure on future protective measures.
As always, prevention is better than cure. But in cyberspace a cure is often needed, with the most prudent organisations having already built into their incident response plans measures to recover business interruption losses.
Andrew Parsons is a partner, and Joel Durston is a senior paralegal at national law firm Bond Dickinson.






